If you only have a few devices on your network, you could easily configure them with static IP addresses and not use a DHCP server at all. In such cases, Internet connectivity will be established more quickly, since computers on the network won’t have to go through the DHCP discovery-offer-request-acknowledge process. As the size of your network grows, however, a DHCP server becomes essential, as keeping track of statically assigned IP addresses will become far too cumbersome.
Moreover, if two nodes have the same IP address, this constitutes an IP address conflict, which is not good, for a variety of reasons:
- It can cause network connectivity problems;
- It can cause network outages, as the network becomes unable to route data to the correct device;
- If two devices have the same IP address, incoming traffic intended for one device may be incorrectly routed to the other device, causing data to be lost or transmitted to the wrong device.
In most cases, if two nodes have the same IP address, the router will recognize one device and ignore the other node, so the only issue is figuring out why one node can’t communicate on the network. Still, it’s beneficial to enable the DHCP server.
Fortunately, configuring OPNsense to act as a DHCP server is relatively easy, and can be done from either the console or the web GUI.
Configuring DHCP from the console is simple, although it doesn’t have as many options. To configure DHCP at the console, do the following:
- At the console, select “Set Interface IP address”
- Select the interface on which you want to enable DHCP (e.g. 1=LAN, 2=OPT1, etc.). For the next steps, x=the interface selected.
- You will have to configure the IP address for the interface. For “Configure IPv4 address x interface via DHCP? [y/N]”, type ‘N’ and press Enter.
- Type in the new x address and the new subnet bit count (probably 24).
- For the interface upstream gateway address, press Enter.
- For “Configure IPv6 x interface via x tracking? [Y/n]”, type ‘N’ and press Enter.
- For “Configure IPv6 x interface via DHCP6? [Y/n]”, type ‘N’ and press Enter.
- Type in the new IPv6 x address and the new subnet bit count (probably 64).
- For the IPv6 LAN upstream gateway address, press Enter.
- The console will query “Do you want to enable the DHCP server on x? [y/N]”. Type y and press Enter.
- Enter the start IP address for the scope and press Enter.
- Enter the end IP address for the scope and press Enter.
- The console will query “Do you want to enable the DHCP6 server on LAN? [y/N]”. You may or may not want to enable the DHCP6 server on the LAN. If so, you will have to enter the start IPv6 address and the end IPv6 address.
If you follow all these steps, you will have successfully configured DHCP at the console in OPNsense. But there are some drawbacks. First, you entered some parameters irrelevant to enabling DHCP. Second, you only configured a fraction of the options available that would be available in the web GUI. If you want to configure many of the options available, you will have to configure DHCP in the web GUI.
To configure DHCP in the web gui, access OPNsense’s IP address and log in. Then do the following:
- In the left sidebar menu, click on Services.
- In the left sidebar menu, click on ISC DHCPv4.
- Click on the interface on which you want to enable DHCP; e.g. LAN
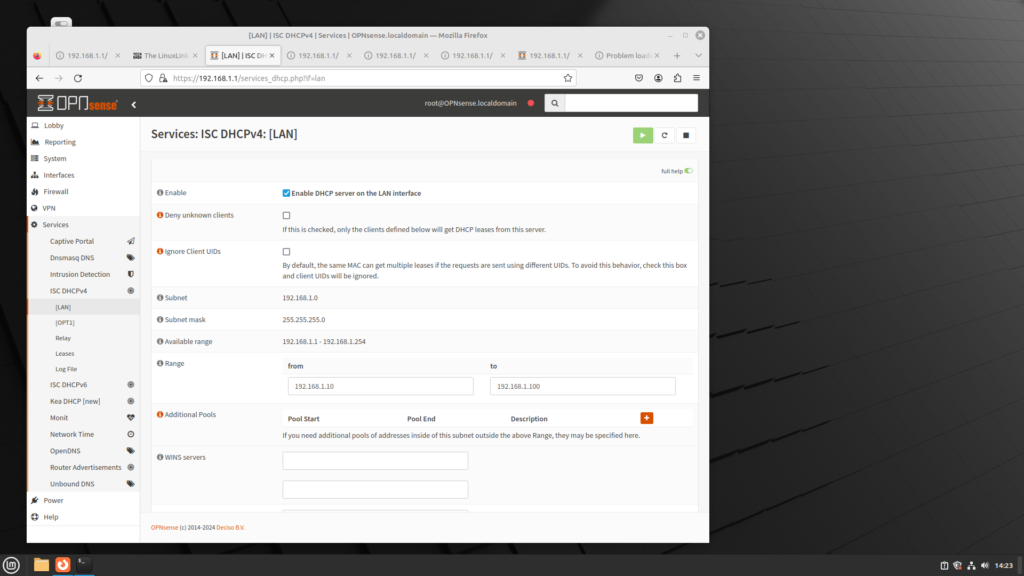
- The page will have a series of DHCP settings; e.g.:
- Enable: This will enable the DHCP server on this interface.
- Deny unknown clients: If this option is checked, then only the clients defined in MAC Address Control will get DHCP leases from the server.
- Range: The scope of IP addresses used for DHCP leases. Note that the range previously specified at the console (192.168.2.10 to 192.168.2.100) is in the edit boxes.
- Additional Pools: You can specify additional pools by clicking on the plus (+) button.
- WINS servers: This allows you to specify the IP addresses of systems running Windows Internet Name Service (WINS), a legacy computer name resolution system that maps NetBIOS names to IP addresses.
- DNS servers: You can specify DNS servers, or leave these edit boxes blank to use the system default DNS servers.
- Gateway: You can use this to specify a gateway IP that is not the IP of this interface.
- Domain name: This is for an alternate domain name.
- Default lease time (seconds): This is used to specify a lease time if clients do not ask for a specific lease time; the default time is 7200 seconds.
- Maximum lease time (seconds): This is the maximum lease time for clients that ask for a specified maximum lease time; the default is 86400 seconds.
- Response delay (seconds): This is the minimum number of seconds since a client began trying to acquire a lease before the DHCP server responds; the default is 0 seconds.
- Interface MTU: This is the minimum transmission unit to use; the default is 68
- Failover peer IP: This is the IP address of an alternate router using Common Address Resolution Protocol (CARP). The default is no IP address.
- Failover split: Use this to specify the load balancing split for a load balancing split; the default of 128 has the primary handling a 50-50 split, while 256 will exclusively use the primary.
- Static ARP: If this option is enabled, only the machines listed in the MAC Address Control will be able to communicate via Address Resolution Protocol (ARP).
- MAC Address Control: The first edit box lists MAC addresses to allow access to; the second edit box lists MAC addresses to deny access to
- DHCP Static Mappings: Here, you can use this to specify an IP address for nodes that require a static IP address; e.g. a web server or an FTP server. Click on the plus (+) icon to add to the DHCP Static Mappings. There you will find the following settings:
- MAC Address: Here, you can specify the MAC address for the Network Interface Card (NIC) on the node. You can click on “Copy my MAC address” to copy the MAC address on the node from which you are accessing the web GUI.
- Client identifier: the identifier of this client.
- IP address: The IP address for the node. The IP address must be part of the subnet for this interface.
- Hostname: Name of the host, without the domain part.
- Description: A brief description of this node.
- ARP Table Static Entry: Enabling this option allows you to create a static ARP table entry for this MAC and IP address pair.
- WINS servers/DNS servers/Gateway/Domain name/Domain search list/Default lease time/Maximum lease time(seconds): See above.
- Dynamic DNS domain: You can use this to enter the dynamic DNS domain, which will be used to register this client.
- NTP servers: Use this to add an NTP (Network Time Protocol) server
- TFTP server: Use this to add a TFTP (Trivial File Transfer Protocol) server and bootfile
- When you are done making changes, click on the Save button at the bottom of the page.
If you have followed all the steps, you have configured IPv6 successfully. But there is still one more question that deserves attention.
Should I Enable DHCPv6?
If your network relies on IPv4, and has more than a dozen nodes, you instinctively want to enable DHCP, which exists because of concern over IPv4 address scarcity. Essentially, DHCP is an efficient manner of allocating scarce resources (private IPv4 addresses). Is this the case for DHCPv6? Not really. The total number of IPv6 addresses is 3.4 * 10^38, so even a randomly chosen IPv6 address will likely not generate an address conflict.
However, there are several advantages to using DHCPv6:
- If VLANs are enabled, then enabling DHCPv6 allows the switch to obtain a global unicast address.
- Enabling DHCPv6 allows the switch to obtain additional information such as an NTP server address or a DNS server address that can be used by the switch.
Keep in mind that a DHCPv6 server does not assign link-local addresses and enabling DHCPv6 on a VLAN does not affect a pre-existing link-local address.
To configure DHCPv6 on an interface, just repeat the same steps as outlined for IPv6, but instead of clicking on Services, ISC DHCPv4 and the interface, click on Services, ISC DHCPv6 and the interface. Much of the parameters for IPv4 are the same in IPv6, with some exceptions:
- Prefix Delegation Range: If your router has a number of subrouters, then you can assign a network to the subrouters. Note that the start and end of the range mus end on boundaries of the prefix delegation size. Ensure that any prefix delegation range does not overlap the interface prefix range.
- Subnet mask: The subnet mask cannot be changed.
It’s up to you to decide to enable DHCPv6, but you can do this easily in OPNsense.