OPNsense is essentially software that works as both a router and a firewall. It is a router because it can route traffic from one network to another; it is a firewall because it can block traffic from one network to another. A firewall is implemented with packet filters, gateways, demilitarized zones, encryption and logging. Network Address Translation (NAT) may be part of a firewall, but it will be discussed in a separate article.
A firewall may not just be a packet filter; it may incorporate higher levels of security: systems for detecting and preventing intrusions for packets that should not be there due to security rules. A firewall may incorporate a honeypot, or a honeynet, which rebuilds a regular network with fake hosts which allows the security team to study attack patterns.
For purposes of this article, we will consider firewall rules. OPNsense is a stateful firewall, which means that it is connection-oriented. The reply packets of a connection do not require a separate rule – they are automatically allowed.
The first match rule makes the order of the rules important. Rules are evaluated from the top down; if the packet matches the rule, this rule is evaluated and the rest are ignored. A blocking rule at the beginning of the ruleset makes the rest of the rules ineffective.
The rules should be sorted by this plan:
- Rules that match packets with bogus addresses are blocked (anti-bogon rule).
- The ruleset – rules in the list – are matched next:
- The upper part of the list should contain rules with detailed information about the source IP, destination IP, and ports (and possibly other details, such as protocol and TCP flags).
- The lower part of the list should host the general rules. These rules filter by source and or destination networks, with or without ports.
- Next, put the rule which silently drops everything that should not appear in the log file.
- Finally, add a rule that denies everything and logs all the denied packets. By default, OPNsense drops unmatched packets, but this rule is easy to switch on and off and is a good rule for troubleshooting.
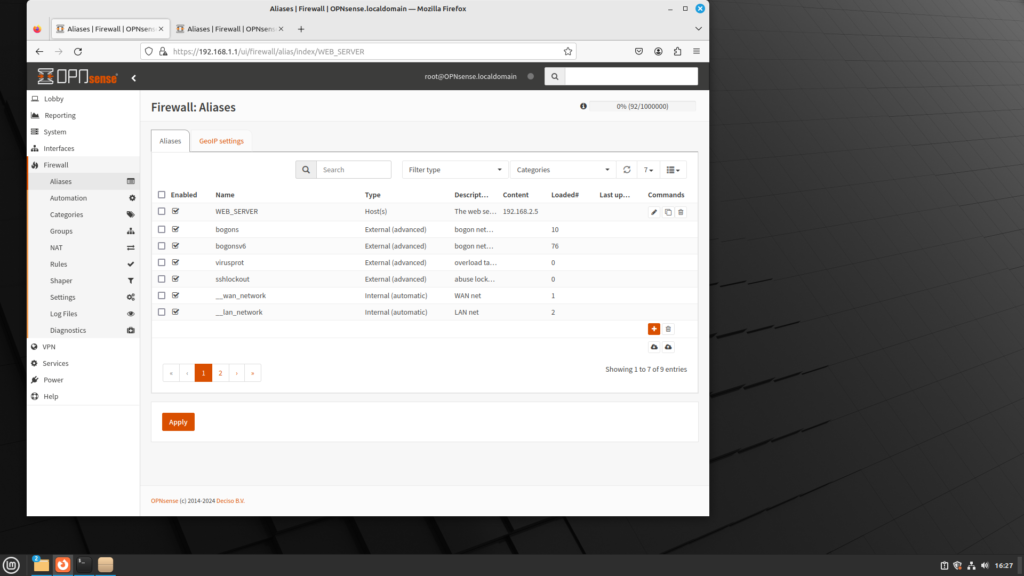
Let’s assume you need a rule to allow traffic to pass on port 80 for the web server, which has an IP address of 192.168.2.5. Do the following:
- Log into OPNsense; on the left sidebar menu, click on Firewall, and click on Aliases.
- Click on the plus (+) icon to add an alias.
- For Name, type in WEB_SERVER.
- For content, type in 192.168.2.5.
- Click on the Save button to save this alias.
- Log into OPNsense; on the left sidebar menu, click on Firewall, click on Rules, and click on OPT1.
- Click on the plus (+) icon to add a rule.
- On Protocol drop down menu, select TCP.
- On the Destination drop down menu, select Single host or Network, then enter WEB_SERVER in the edit box.
- On the Destination port range, select other, then enter 80 in the edit box.
- In the Description field, enter “Allow HTTP to web server”.
- Click on the Save button at the bottom of the page to save the rule, then click on Apply Changes at the top of the screen to reload the firewall rules.
