Now that we have set up the WAN and LAN networks, we should consider configuring the DMZ.
The DMZ (demilitarized zone), or screened subnet, is physical or logical subnetwork that exposes an organization’s external-facing servers to the Internet. The purpose of the DMZ is to add an extra layer of security to a LAN. With a DMZ, an external node in the DMZ can only access hosts in the DMZ, while the rest of the network is hidden behind a firewall.
To configure the DMZ, three steps are necessary:
- Enabling the DMZ
- Adding firewall rules to the DMZ
- Testing the DMZ to confirm security
In this article, we will cover all three steps.
Enabling the DMZ
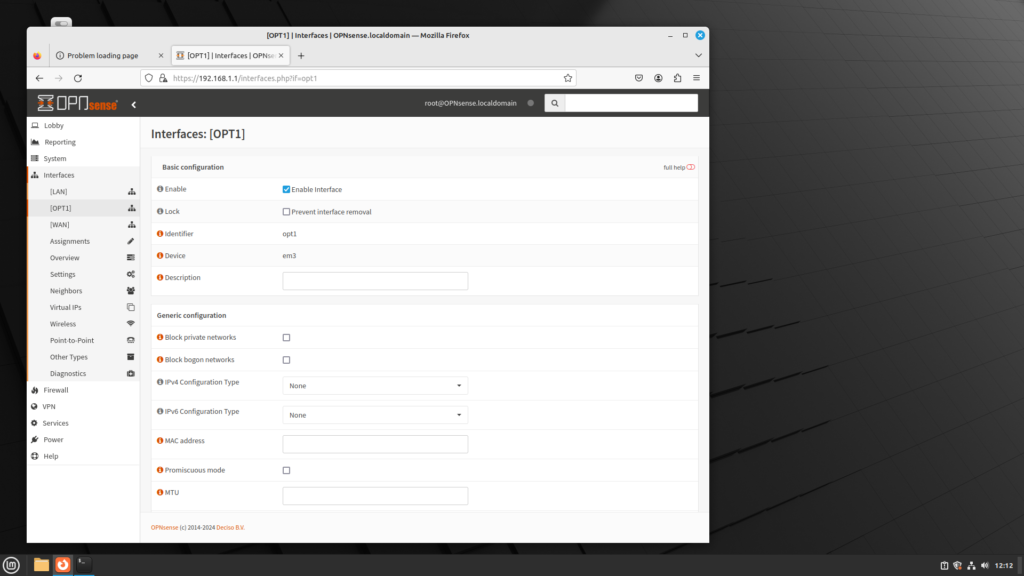
In order to enable the DMZ (which is referred to as OPT1), do the following:
- Log into the web GUI.
- On the left menu sidebar, click on Interfaces.
- On the left menu sidebar, click on OPT1.
- The OPT1 web page offers a number of different parameters:
- Description: This is where you can enter a brief description
- Block private networks/Block bogon networks: Just as in the configuration page for WANs, you can prevent private addresses from being sent and prevent reserved and unassigned IP addresses from being sent. For most cases, these options should be left unchecked.
- IPv4/IPv6 Configuration Type: Unless you have an upstream DHCP server, you should select Static IPv4/Static IPv6.
- MAC Address: You can enter a different MAC address, which enables MAC spoofing.
- MTU/MSS/Duplex and Speed: You can alter the maximum transmission unit (default is 1500), the maximum segment size (default is 536 for IPv4, 1220 for IPv6). You can also change the duplex and speed, from 10 Base T to 1000 Base T, and select between half and full duplex.
- Static IPv4/IPv6 Configuration: Since you selected static configuration, you must enter an IP address here. If you used 192.168.1.0/24 for the LAN, you likely should enter 192.168.2.1 here for IPv4, and fd00:2::1 for IPv6.
- IPv4/IPv6 Upstream Gateway: This is for a separate upstream link; it should be left as Auto-detect.
- Uses IPv4 connectivity: If IPv6 is supplied over a PPoE connection, you need to check this option.
- When you are done making changes, click on the Save button at the bottom of the page, then click Apply Changes at the top of the page.
Adding Firewall Rules to the DMZ
As of now, we have enabled and configured the DMZ interface. But the reason we added a DMZ was so front-facing servers could be exposed to the Internet, with all other nodes behind the firewall. But for that to happen, we must add firewall rules.
- On the left menu sidebar, click on Firewall.
- On the left menu sidebar, click on Rules.
- On the left menu sidebar, click on LAN.
- There are two pre-defined rules to ensure that the LAN can interact with the Internet: the default “Allow LAN to any” rule and the default “Allow LAN IPv6 to any” rule. We need to clone these two rules for the DMZ (OPT1).
- For the “Allow LAN to any rule”, click on the clone (depicted as two pieces of paper) icon to copy it. This rule should remain the same, with the following exceptions:
- The Interface should be changed to OPT1.
- The Source should be changed to OPT1 net.
- The Description should be changed to “Default allow DMZ to any rule”.
- Click on the Save button on the bottom of the page to save the rule.
- For the “Allow LAN IPv6 to any rule”, again click on the clone icon to copy it. This rule should remain the same, with the following exceptions:
- The Interface should be changed to OPT1.
- The Source should be changed to OPT1 net.
- The Description should be changed to “Default allow DMZ to any rule”.
- Click on the Save button at the bottom of the page to save the rule, then click on the Apply Changes button at the top of the page to reload the firewall rules.
- Now the DMZ can interact with the Internet, but the LAN still has to interact with the DMZ. We can make rules by cloning the default rules and making changes to them.
- For the “Allow LAN to any rule”, click on the clone icon to copy it. This rule should remain the same, with the following exceptions:
- Destination should be changed to OPT1 net.
- Description should be changed to “Allow LAN to DMZ rule”.
- Click on the Save button at the bottom of the page to save the rule.
- For the Allow LAN IPv6 to any rule”, again click on the clone icon to copy it. This rule should remain the same, with the following exceptions:
- Destination should be changed to OPT1 net.
- Description should be changed to “Allow LAN IPv6 to DMZ rule”
- .Click on the Save button at the bottom of the page to save the rule, then click on the Apply Changes button at the top of the page to reload the firewall rules.
Test the Network to Confirm Security
Now you have added the DMZ interface and the firewall rules so that the LAN can interact with the DMZ, but the DMZ cannot interact with the LAN. But we don’t know whether it works or not until we add a node to both the LAN and the DMZ to test the network. To confirm that the network works, do the following:
- From the DMZ node, ping a server on the Internet. The ping should be successful.
- From the LAN node, ping the DMZ node. The ping should be successful.
- From the DMZ node, ping the LAN node. The ping should not be successful.
If all three criteria are met, then it looks like the network works, and you can begin deploying your Internet-facing servers. You should be aware that you will have to configure NAT and a firewall rule for each server, and you will likely have to test connectivity to the server as well. But by following these steps, you will have successfully deployed a DMZ/screened subnet in OPNsense.